To allow read 4 and write 2 you set the user permission to 6. Which of the following does a secure website use to safeguard transmitted information.

Security Privacy By Design Principles
Haven runs an online bridal store called Haven Bridals.
. True E-commerce sites use Transport Layer Security TLS to encrypt data and protect you. Another process that is used to protect the data transmission in VPN is called tunneling. Information that is being transmitted over an electronic communications network Implementation Specification.
If you want to allow multiple permissions simply add the numbers together eg. Which of the following does a secure website use to safeguard transmitted information. Web APIs connect between applications and other services or platforms such as social networks games databases and devices.
Integrity controls Implement security measures to ensure that. News360 is a search engine because it gathers organizes and then distributes web content. Define a method calcPyramidVolume with double data type parameters baseLength baseWidth and.
O the web apps server What are hits that search engines list. In addition data is decrypted once it exits the Tor Network. From fraud and identity theft True.
True False Question 21 25 points What does a URL that starts with https signify. You can use encryption protocols at home to protect the data that you send online. The process that is used to protect data in a VPN is referred to as tunneling.
The process of verifying the identity of a user. Run the program file or script. It helps provide data security for sensitive.
Additionally Internet of Things IoT. News360 is a search engine because it gathers organizes and then distributes web content. Most websites use the data encryption mechanisms TLS Transport Layer Security or SSL Secure Sockets Layer to protect site and user data as its transmitted to and.
The data is transmitted through secured L2TP protocol or PPTP protocol. Encryption is a process that scrambles readable text so it can only be read by the person who has the secret code or decryption key. Designed to support both voice and data communications.
The use of different nodes in the Tor Network to promote anonymity for example can slow data transmissions. Rogelio wants to buy appliances for his newly leased apartment. Question 20 options.
However there are different threats associated with. Transport Layer Security TLS Transport Layer Security formerly known as Secure Sockets. Here Are 10 Types of Information You Must Protect.
View Test Prep - TfS Quiz Twodocx from IT 101 at Bentley University. TfS Quiz Two Cloud storage refers to the storage of data on _. There are multiple secured protocols that are used for the purpose of secured.
AIs should adopt secure and internationally-recognised strong encryption algorithms to protect the confidentiality of customers information transmitted over external networks including the. Which of the following does a secure website use to safeguard transmitted information. In order to protect your information located online you need security controls and encryption in place.
Email is a commonly used method to transmit confidential data and information and considered safe by most.

What Is A Pci Audit How To Get Your Business Ready Hyperproof

Website Security How To Secure Your Website Sucuri
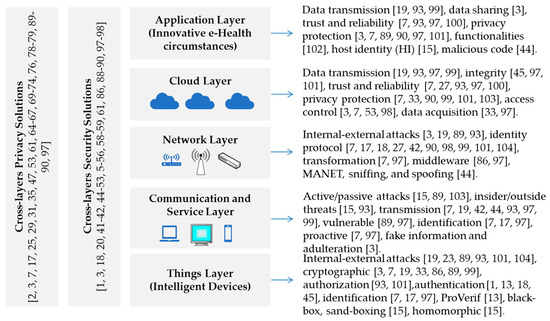
Symmetry Free Full Text Security And Privacy In Iot Cloud Based E Health Systems A Comprehensive Review Html

Land Use Induced Spillover A Call To Action To Safeguard Environmental Animal And Human Health The Lancet Planetary Health

Top 15 Tips For Securing Your Personal Information Bitlyft Cybersecurity
What Are The Top Secure Data Transmission Methods Penta Security Systems Inc
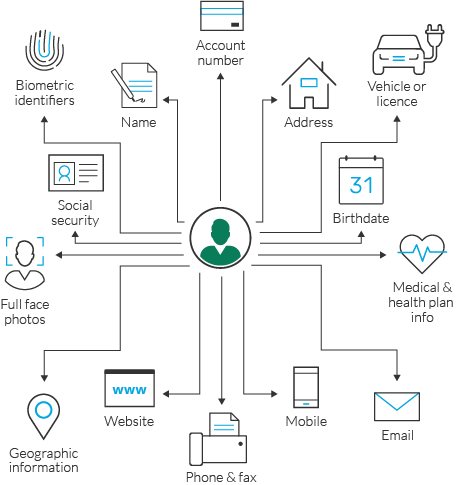
What Is Personally Identifiable Information Pii Data Security Imperva

Chrome Extensions Requirements For Privacy Policy And Secure Handling Privacy Policies
0 comments
Post a Comment